 |
CRYPTOGRAPHY |
| << FIREWALLS |
| HASH FUNCTION AND MESSAGE DIGEST >> |
E-COMMERCE
IT430
VU
Lesson
22
CRYPTOGRAPHY
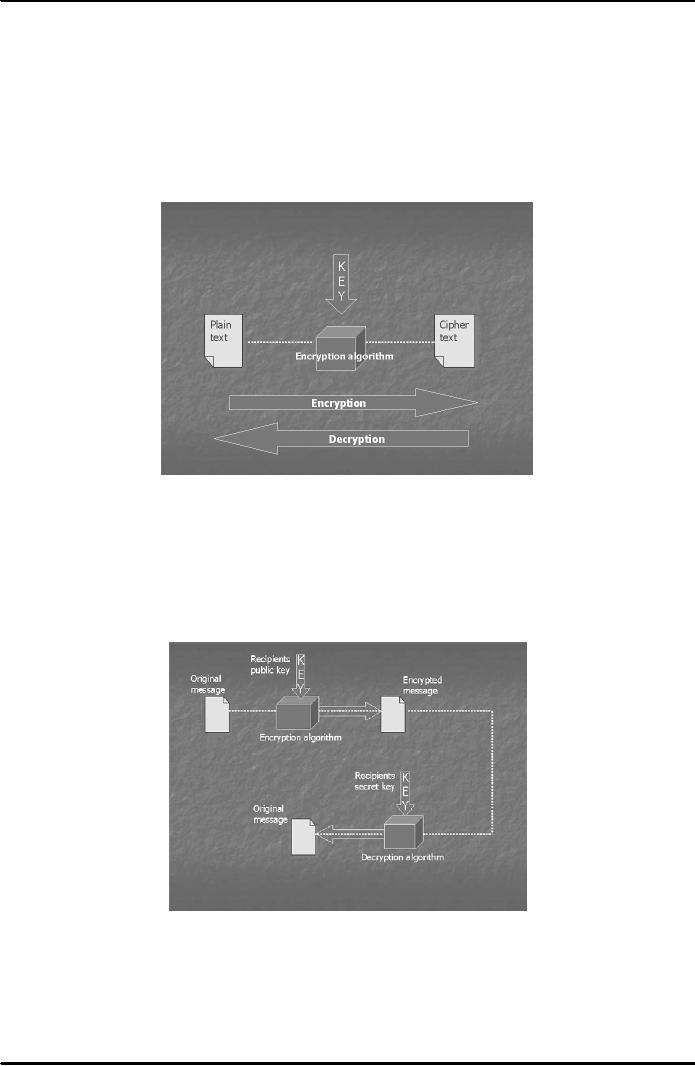
Cryptography is a
collection of mathematical techniques
used to ensure confidentiality of
information. The
process
of scrambling a message with the
help of a key is called
Encryption. The process of
unscrambling a
message
using an appropriate key is called
decryption (see Fig. 1).
Keys are numbers or
characters that are
randomly
generated with the help of
some cryptographic algorithm. Pretty Good
Privacy (PGP) is the name
of a
popular cryptographic system which is
available for general public
use. There are two types
of
cryptography -
Symmetric and Asymmetric
cryptography.
Fig.
1
Symmetric
Cryptography
In
symmetric cryptography same keys
are used for encryption
and decryption.
Asymmetric
or Public Key Cryptography
In this type a
pair of public and private
keys is used for encryption
and decryption (Fig.
2).
Fig.
2
Digital/electronic
signature
An electronic
signature means any letters,
numbers, symbols, images,
characters or any combination
thereof
in electronic
form applied to an electronic document which
can ensure authenticity, integrity
and non-
repudiation.
It uses public key cryptography (Fig.
3). Authenticity
means
that the message is from
a
particular
source/individual. Integrity means
that the message has not
been altered during
transmission.
100
E-COMMERCE
IT430
VU
Non-repudiation
means that the execution of the digital
signatures cannot be denied by the one
who is
alleged
to be the
Fig.
3
Digital
certificates
These
are the certificates in electronic form
which establish whether or not a
public key belongs to
the
purported
owner. A digital certificate at least
comprises a public key,
certification information (name,
ID
etc.)
and electronic signatures of a
certification authority. Digital
certificates are prepared
according to a
generally
accepted format called X.509
standard format.
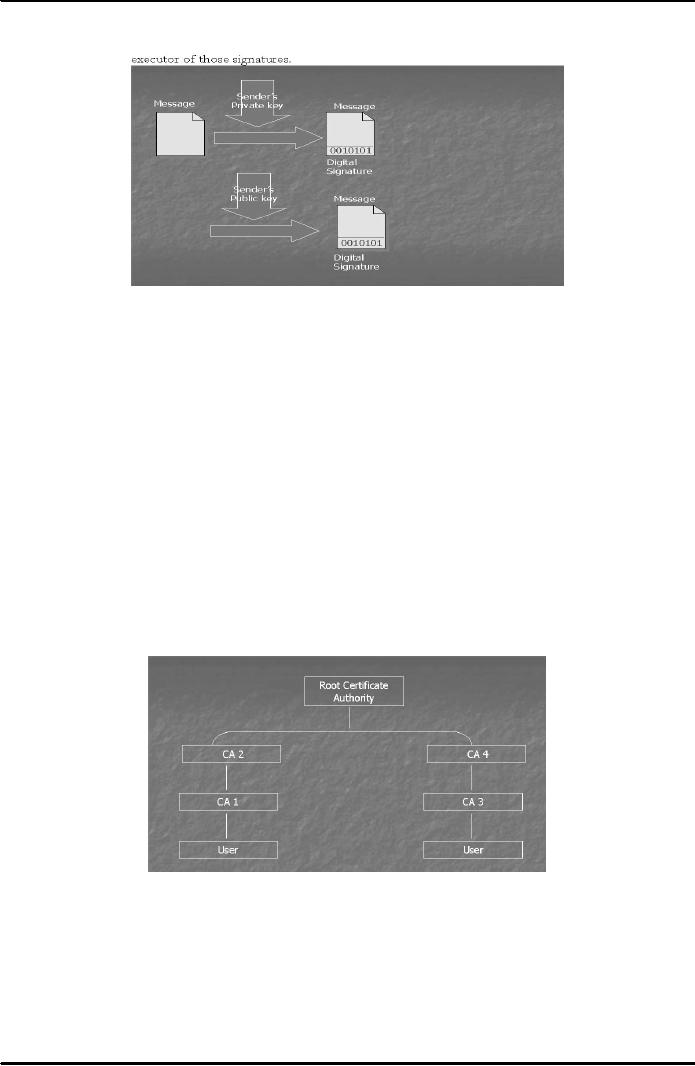
Certification
authority (CA)
A
certification authority is defined to be
a trusted public/private body
that attests the association of
a
particular
individual with his/her corresponding
public key. A CA signs
digital certificates with
its private
key.
There are many CAs working
in the field but the pioneering or the
most reputed CA is Verisign
which
is
based in America.
Certification
authorities work in a hierarchical fashion. There is
the CA at the top called root CA (the
most
reputed
CA). It can issue
certificates to CAs working
below it and those CAs' can
further issue
certificates
to CAs
working under them. In this fashion a
hierarchy of CAs is developed with
each CA confirming the
public
key of the CA below it through a
digital certificate. This concept is
elaborated in Fig. 4 below.
Fig.
4
Assume
that I want to send an encrypted or a
confidential message to Mr. A.
For that I need to know
his
public
key. I can access a machine
called key server and
try to find his public
key against his
particulars
(name,
address, id etc). I may
discover that a CA, CA1
below in hierarchy has
issued a digital certificate to
Mr. A
against his particulars and
has signed it with its
private key. If that CA holds a
reputation that I can
trust it
then I would rely upon that
public key and use it
for encryption. Otherwise, I should go up
the
hierarchy
and see whether there is a certificate
issued by CA2 certifying the
public key of CA1. If
that
certificate is
found then ideally I should go further up
the hierarchy to check that the
CA, above CA2
which
101

E-COMMERCE
IT430
VU
is
root CA in this case has
issued certificate to CA2 or not. In this
manner I can check the
certificates upto
the
root CA.
If all
the certificates in the chain are
available, then it should provide me the
maximum trust that this
key
actually
belongs to that particular user.
However, if the chain is broken or
any certificate is missing in
between
that might cause a dent in my trust on
that public key. I would
then be hesitant to use that
public
key
appearing to be that of Mr. A. It is
all a web or the model of trust. The
greater is the reputation of a CA
the
more trust I shall have in the
certificate issued by it authenticating the public
key of a user. The CAs
at
the
top level of hierarchy carry
more trust. So, if Mr. A has
a certificate directly from the root CA,
his public
key
would be most trust worthy. In
case he has a certificate directly from
Verisign, the most reputed CA in
the
world then I should have
maximum trust that this public
key must be that of Mr. A
whom I know. I
should
have trust that if Verisign
has issued the certificate it would
have done detailed investigation
before
issuing
it to Mr. A. His name,
address, identification would
have been properly verified
or confirmed before
associating
a public key with him
through the certificate. If you
are obtaining a certificate from a
top level
CA,
which is more reputed, you
have to pay more to that
CA. So Mr. A has to pay
relatively more to the
root
CA if he wants to obtain a certificate directly
from the root CA. There are
different levels of
certificates
attaching different levels of trust
with them. We may have
class, A, B or C type certificates.
A
Class
A certificate would have more trust
attached to it. Of course,
one has to pay relatively
more to get a
class
A certificate from a CA as compared to
class B or C. However, in class A, a
greater level of
investigation
would be involved before issuing a
certificate to someone.
You
may have noticed that the
role of a Certification Authority is
analogous or similar to a passport
office.
The
issuance of passport by the passport
office attaches credibility
that this particular person is entitled
to
travel.
However, the passport is not
issued by the office until detailed
enquiry/verification about the
identity
of the
person is made. Once a
person holds the passport, that confirms
that this particular person
whose,
name,
address etc. is appearing on the
passport is entitled to travel. Similarly, if a
digital certificate is issued
by a reputed CA
that would confirm to other
people that this particular public key
certified by the CA
belongs
to this individual only.
There is a
reason why we use the
concept of CAs. We use it
for the verification of identify of a
person. This
is
probably the best solution
envisaged for such
verification, though it may
have certain loopholes in it.
You
can
realize that the best thing
is that Mr. A personally
hands over his public
key. On the other hand if I
try
to
trace his public key
against his particulars
(name, address, and
identification no.) on a key server
there is a
possibility
that I end up discovering
that there are three,
four, five different public
keys against the
particulars
of same Mr. A. Assume that
all of them have been
certified by different CAs.
Now, I am
confused
that which of these is
genuine so that I can use
it. Indeed, only one of them
is genuine and the
rest
are
fraudulent keys registered by
fraudulent people using particulars of
Mr. A. In this situation I would
use
and
rely upon that public key of
Mr. A that has been
certified by the most reputed CA among
all the CAs. I
would
treat others as fraudulent. The objective
of getting fraudulent keys is to
intercept/receive the
messages
intended to be sent to a particular receiver.
So, if someone intends to receive the
messages
delivered
for Mr. A, he may register
the key against his
particulars and get a certificate in this
behalf. Note
that
CAs are supposed to issue
the certificate after proper enquiry, otherwise they
may also be held
liable
under
different laws.
Despite the
loophole that fraudulent
keys can be obtained in this set up, this
system of certificates is
believed to be the
best for confirming
authenticity of a person. Imagine
that I want to send an
encrypted
message
to someone in Canada from
Pakistan. It would not be
practical that first I
contact him in Canada
and in
some manner obtain his
public key and then
send him the message using
that. It would be more
convenient,
practical and time saving
that I go to a key server,
find his public key
against his particulars
and
check
whether it is certified by a reputed CA. In
other words if the certificate of a well
respected CA is there
to
authenticate his public key
then I can use that
public key. Behind this
system of certificates and
CAs, the
idea
is to make internet communication global in
nature such that the
authenticity of individuals is
also
ensured
at the same time.
102
Table of Contents:
- E-COMMERCE
- WHAT IS A NETWORK
- HOW MANY CLASS A, B, C NETWORKS AND HOSTS ARE POSSIBLE
- NETWORKING DEVICES
- BASICS OF HTML 1
- BASICS OF HTML 2
- TEXT BOXES, CHECK BOXES, RADIO BUTTONS
- FRAMES AND IMAGES IN HTML
- TAG ATTRIBUTES, SOUNDS FILES, ANIMATIONS
- STYLE SHEETS 1
- STYLE SHEETS 2
- SOME USEFUL STYLE SHEETS PROPERTIES
- JAVA SCRIPTING 1
- JAVA SCRIPTING 2
- JAVA SCRIPTING 3
- JAVA SCRIPTING AND XML
- CLIENT AND SERVER SIDE PROCESSING OF DATA
- APPLETS, CGI SCRIPTS
- MAINTAINING STATE IN A STATELESS SYSTEM
- INTEGRATION WITH ERP SYSTEMS
- FIREWALLS
- CRYPTOGRAPHY
- HASH FUNCTION AND MESSAGE DIGEST
- SYMMETRIC KEY ALGORITHMS
- VIRTUAL PIN PAYMENT SYSTEM
- E-CASH PAYMENT SYSTEM 1
- E-CASH PAYMENT SYSTEM 2
- SECURE SOCKET LAYER (SSL)
- E-BUSINESS: DISADVANTAGES OF E-BUSINESS
- E-BUSINESS REVENUE MODELS
- E-MAIL MARKETING
- CUSTOMER RELATIONSHIP MANAGEMENT (CRM)
- META INFORMATION
- DATA MINING
- CONFIDENCE AND SUPPORT
- ELECTRONIC DATA INTERCHANGE (EDI)
- PERSONAL FINANCE ONLINE
- SUPPLY CHAIN
- PORTER’S MODEL OF COMPETITIVE RIVALRY
- BARRIERS TO INTERNATIONAL E-COMMERCE
- ELECTRONIC TRANSACTIONS ORDINANCE, 2002 - 1
- ELECTRONIC TRANSACTIONS ORDINANCE, 2002 - 2
- ELECTRONIC TRANSACTIONS ORDINANCE, 2002 - 3
- GLOBAL LEGAL ISSUES OF E-COMMERCE - 1
- GLOBAL LEGAL ISSUES OF E-COMMERCE - 2